Chacha20 Algorithms¶
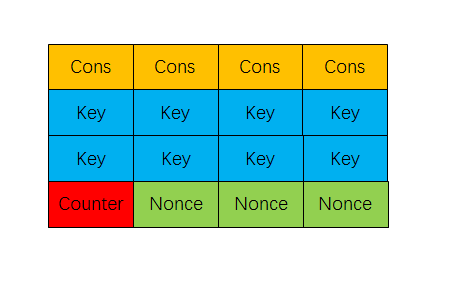
Chacha20 is a cipher stream. Its input includes a 256-bit key, a 32-bit counter, a 96-bit nonce and plain text. Its initial state is a 4*4 matrix of 32-bit words. The first row is a constant string “expand 32-byte k” which is cut into 4*32-bit words. The second and the third are filled with 256-bit key. The first word in the last row are 32-bit counter and the others are 96-bit nonce. It generate 512-bit keystream in each iteration to encrypt a 512-bit bolck of plain text. When the rest of plain text is less 512 bits after many times encryption, please padding to the left with 0s(MSB) in the last input data and remove the same bits unuseful data from the last output data. Its encryption and decryption are same as long as input same initial key, counter and nonce.
XChacha20 is a variant of original Chacha20 to support Longer nonce of 192bits. Its implementation is similar to Chacha20.
Implementation¶
Chacha20 consist of 2 parts: initialization state and encryption as shown in the following picture:
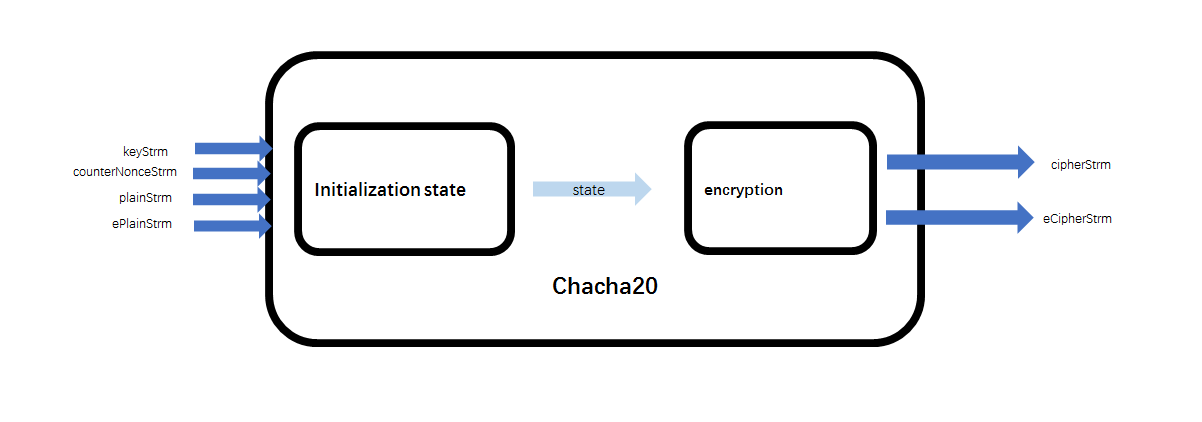
Initial state is generated by the input 256-bit key, 32-bit counter and 96-bit nonce. In the encryption, a new 512-bit key is generated and is used for doing XOR with 512-bit plain text, then output a cipher block in each iteration.
Performance (Device: U250)¶
| II | CLB | LUT | FF | DSP | BRAM | SRL | URAM | CP(ns) |
|---|---|---|---|---|---|---|---|---|
| 1 | 3029 | 20535 | 21112 | 0 | 0 | 64 | 0 | 2.989 |